Best Firewall as a Service (Fwaas Vendors)
Firewall-as-a-service or Fwaas– is a cloud solution that protects networks from malicious traffic and viruses a they are relatively new kind of firewall. They don’t just block or allow traffic based on IP addresses and ports, they go a step further to analyze traffic and make decisions based on a set of predefined business rules.
The rise of cloud applications calls for a change in security solutions, which SASE architecture can provide:
- Data confidentiality for transferred and stored data
- Granular access control for these protean data (files, structured databases, unstructured databases)
- Latency when these applications are accessed from anywhere in the world
Why FireWall-as-a-Service
Cloud firewall providers can go all-out in their strategy to protect the firewall from attack. Serving many customers gives them the cost base that allows them to invest in clusters of servers with failover backup hardware, technicians working in shifts around the clock, and a worldwide perspective to cybersecurity.
On the plus side, a cloud-based solution requires no maintenance as it is handled by the vendor. These solutions typically have built-in redundancy or high availability features. The vendor also typically handles system backups.
If a new attack vector arises, the firewall provider has to come up with a solution very quickly and roll that out to all of its customers. An FWaaS provider does the same thing but rather than sending out updates to its customers all over the world, it just needs to update the software on its own servers and every customer is instantly protected by the adjustment.
The distributed software strategy of traditional onsite firewalls opens up the risk of a customer blocking automatic updates, neglecting to install a patch, failing to read a security warning notice, or just not securing their systems properly. Letting the firewall provider host the security system removes all of those weaknesses.
Our Top 5 Best Cloud-Based FWaaS
We’ve compiled a list of the five best could-based Firewall-as-a-Service provider. They’re all from reputable suppliers and offer great value for your money. We can’t really recommend one over the others as they’re all excellent products.
1. ZeroOutages Orion
The ORION cloud security services are hosted within the ZeroOutages CloudDMZ for customers that wish to ensure the greatest possible protection for their network. ORION provides an application and content aware platform for managing end-user traffic while sandboxing potentially malicious file. With full Active Directory integration ORION provides per-user control over web site access via a variety of categories which are updated dynamically.
Orion
is next generation SD-WAN with
Content Filtering, IDS/IPS and Integrated Remote Access.The ORION services each incorporate next generation SD-WAN capabilities, including built-in security services. However they can still be paired with existing firewall and security solutions. Each ORION service also comes with cloud managed content filtering services and an assigned virtual IP address for seamless failover across ISP connections. Works by sitting in front of any existing firewall deployment or can replace a firewall, as needed.
ZeroOutages ORION services include the HomeOffice, SMB, and Enterprise versions. Each incorporates next generation SD-WAN with virtual IP addressing, cloud managed content filtering, and built-in remote access capabilities for remote workers. The HomeOffice version of the product does not have remote access, but does have an integrated wireless access point with home and office SSIDs for easy home deployments.

Remote Access
Solutions
Quickly setup and easily manage remote access permissions with the ORION platform. All users can be managed from our portal and various access levels can be applied based on group privledges.

Industry Leading
Content Filtering
Dynamic category-based content management for organizations of all sizes. This service is easily managed in the cloud, includes custom policies, malicious site blocking and detailed reporting.
2.CrowdStrike Falcon Firewall Management
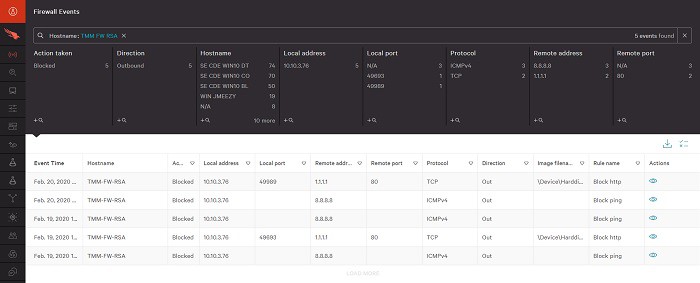
CrowdStrike Falcon is an enterprise security suite that delivers next-gen AV and endpoint protection. The Falcon system includes a number of modules and the Firewall Management component is an optional extra.
As with the endpoint protection system from CrowdStrike, the Falcon Firewall Management module is resident in the cloud and also relies on an installed agent onsite to gather data and implement workflows. The tool protects the network and each endpoint, creating a two-phase protection service.
The CrowdStrike Falcon dashboard is delivered from the CrowdStrike server and accessed through any standard browser. That means that it is available anywhere and the administrator does not need to be in the same location as the protected system. It also means that remote workers and different sites can all be protected and managed from one central console.
Even though it is a distributed system, the central Firewall Management console enables administrators to impose the same rules and policies on all protected devices. This unifies the firewall, making it operate as a single entity.
Although there are onsite elements to the CrowdStrike Falcon system, the bulk of processing, such as threat hunting and traffic scanning, is carried out on the cloud servers. This greatly reduces the hardware requirements of the business using the service. It also means that network administrators don’t need to worry about keeping the system updated or providing failover hardware because all of those issues are dealt with by the CrowdStrike staff.
Falcon is available in four editions: Falcon Pro, Falcon Enterprise, Falcon Premium, and Falcon Complete. None of those plans include the Firewall Management module automatically – it has to be added on. The Falcon Complete option is a bespoke plan that includes a managed security service and a Breach Prevention Warranty. Potential customers can get a 15-day free trial of the Falcon security suite.
EDITOR’S CHOICE
CrowdStrike Falcon Firewall Management is our top pick for FWaaS because it provides a nice blend of network and endpoint protection. The service is charged for by subscription, so there are no upfront hardware or software costs with this security system. Thanks to the cloud architecture of CrowdStrike Falcon Firewall Management, administrators can include protection for remote workers and other sites into the home network protection plan.
Get a 15-day free trial: go.crowdstrike.com/try-falcon-prevent.html
OS: Cloud-based
3. Zscaler Cloud Firewall
Zscaler built its FWaaS system with virtual offices in mind. The company noted that traditional business practices that involve crowding all workers into an office space is no longer valid. This system offers a solution that allows remote workers to safely connect to the business network and enjoy protection from the corporate firewall while working.
The software for the firewall service doesn’t need to be resident on the protected computer. Instead, the service just protects the connection, checking all traffic to make sure that the worker’s device doesn’t pass viruses over to the main system.
The Zscaler solution is a great idea for businesses that deploy a BYOD strategy as well as those that regularly deal with home-based workers. Whether the protected device is owned by the company or the user, the firewall service doesn’t touch the device. This means that there are no heavy background processes to drag down the performance of the device. It will even protect communications via mobile equipment.
The remote inclusion service sounds like a VPN. However, Zscaler points out that its system doesn’t just protect the privacy of connections, it implements firewall policies within the secure connection. So, it could be seen as a VPN+ – it is certainly a proxy service as all traffic needs to flow through the Zscaler server, which acts as an edge system between the company’s network and the wider internet.
Zscaler is coy about its pricing for the Cloud Firewall and it doesn’t offer a free trial. However, it is possible to get a demo of the firewall service.
4. SecurityHQ Managed Firewall
SecurityHQ goes one step further than just hosting a firewall service, it also offers the management of the firewall. This is a great option for businesses that don’t have their own IT team or those that do but don’t have specific cybersecurity skills onsite.
IT specialists with cybersecurity expertise are hard to find and, as in any market with a shortage, their wage levels are high and constantly rising. Even if you manage to hire an expert to manage your firewall, it won’t be long before another business outbids you, leaving you with the need to go through the hiring process again.
Managed services plug the skills gap. This is a particularly useful option for small businesses that just don’t have the volume of traffic that would justify the expense of a dedicated cybersecurity expert on their staff. The other option that small businesses usually go for is to dump the responsibility for the firewall’s installation and management on an unskilled manager.
The SecurityHQ service is staffed around the clock and is hosted on a cluster of servers, which guarantees persistence. The system is run along with ITIL standards and it enables businesses to be fully compliant with PCI DSS, HIPAA, SOX, NERC, and CIP.
SecurityHQ’s Managed Firewall is a bespoke service. There is no price list or plan schedule. You need to contact the company and ask for a free security audit in order to get a quote.
5. Secucloud Firewall as a Service
The Secucloud Firewall as a Service uses AI-based machine learning techniques to identify traffic that is out of the ordinary. This is the hallmark of a next-gen security system and it reduces the incidences of false-positive anomaly identification.
Traditional firewalls are difficult to calibrate. They require a list of identifying characteristics against which all traffic needs to be compared. That requires heavy processing of data that can slow down transmissions and cause genuine traffic to be blocked. The next-gen approach adjusts the pattern of regular traffic according to a reputation grading of the source and destination addresses for the connection. This speeds up processing for genuine traffic.
A second advantage of the Secucloud system is the company’s Global Cloud Intelligence feed. This is a blacklist system that gathers live transaction reports from all over the world, identifying hacker addresses and the file names used for detected virus attacks. The blacklisting of suspicious sources also cuts down processing time for live data.
Secucloud is a hosted system, which means that it operates as a proxy, channeling all internet traffic that passes in and out of the protected network. The connection between the client’s system and the Secucloud server is protected with a VPN.
6. Cato Networks SASE
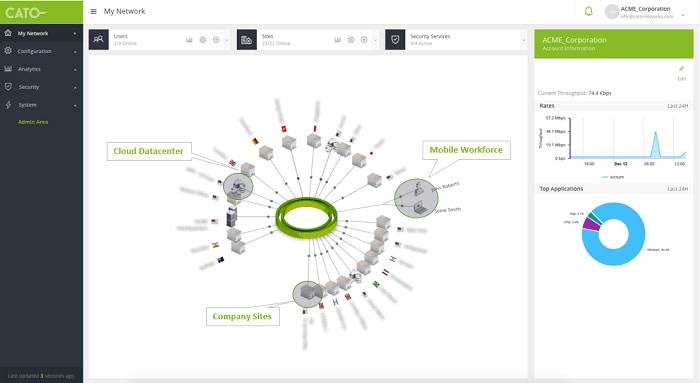
Cato Networks has developed a cloud-based security platform, called SASE, which stands for Secure Access Service Edge. This system offers a range of edge services including an FWaaS. This strategy makes sense because there are a number of services that a proxy service can offer to businesses and they can all be performed simultaneously.
Other edge services in the SASE system include an SD-WAN, WAN optimization, a content delivery network, and a DNS service. This is supplied by a network of servers in many locations rather than just one data center. The system also includes a secure remote access system for home-based workers so that they can connect to the company network and be protected by the FWaSS while on company business. This system will also include mobile devices in the network.
The FWaaS is part of a bundle of security services offered by SASE, which also include a next-gen anti-virus, a managed threat detection and response, and a managed intrusion prevention system.
The Cato Networks SASE system is very comprehensive and so it takes some time to fully understand. It deals with all communications issues that any business connected to the internet could have. The FWaaS deploys deep packet inspection to examine all incoming and outgoing traffic, enabling businesses to block access to certain websites and it also implements data loss prevention strategies. The firewall checks on the protocol of each transmission and adapts its control standards accordingly.
The Cato Network SASE is a very good option both for very large businesses that want to centralize the security measures that cover many sites and it is also appropriate for small businesses that use freelance workers and have most of their staff out on-site or that operate a virtual office.
